Access to private port of your application - Zscaler Private Access
Introduction
The digital transformation describes the move from accessing physically to accessing online to services.
In this context, Thales provides the Trustnest to help users exposing their applications online (meaning accessible from internet, generally using HTTPS). To maintain a strong level of security, even if the application is exposed on internet, Identity & Access Management is put in place to enforce MFA and put additional security mechanisms in place. If you want to learn more about it, have a look to the IAM online doc
But, as developer you may need to access to your virtual machines using SSH, or administrate your databases. Opening these ports on internet is forbidden for security reason (most administrative protocol does not support MFA). Trustnest provides a VPN Point to Site solution based on Zscaler Private Access.
The purpose of this documentation is to describe the solution in place, the known limitations and what to do to get an account.
Service enabled for Innovate and Industrialize
Description
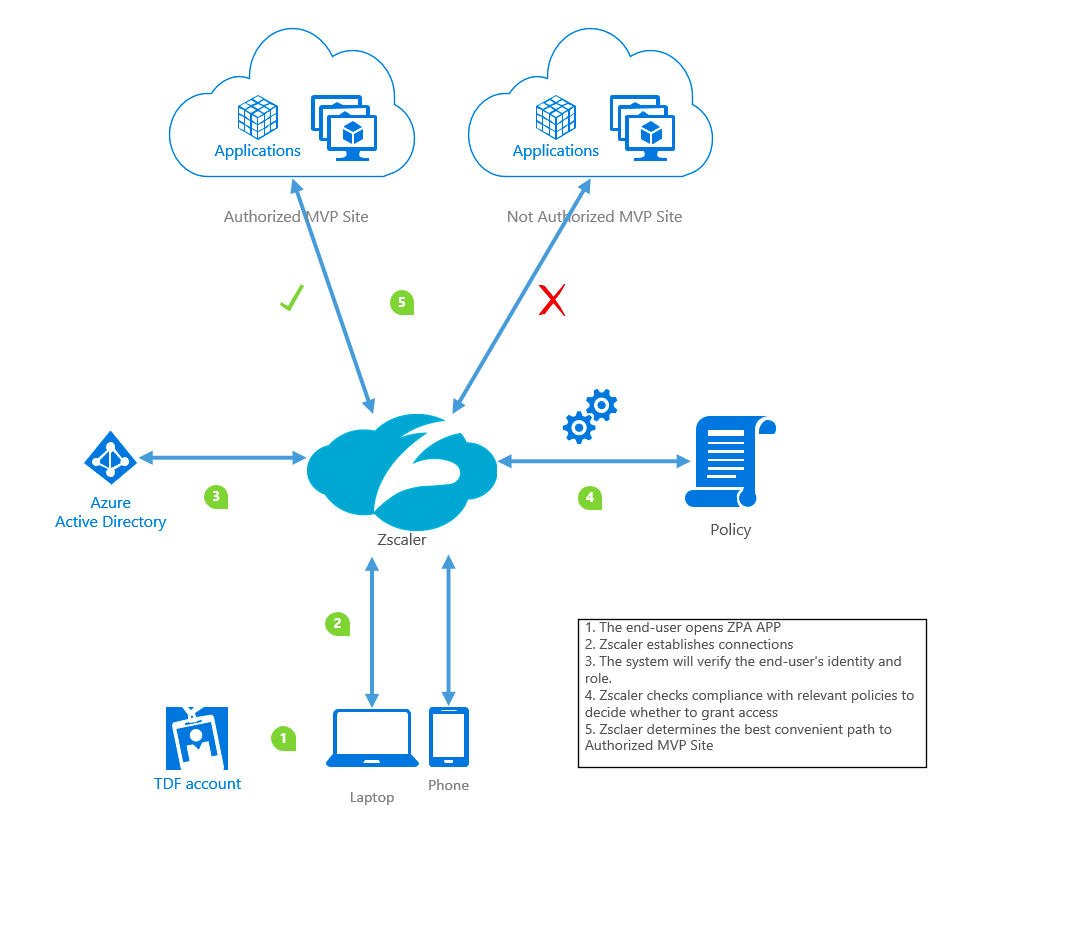
Now with Zscaler private access we can provide a secure connection for end-users whom can only use specific displayed applications/ resources.
Below is the description of the technical solution :
Prerequisites
Know at the enrollement level your Post TNAP will installed Zscaler agent, Without ZPA active.
- First, ask to be added to the ZPA licence Users, See Post iT, Request Add-on license
- Second, your vnet must refer to one of this IP Plan: TDP or Thales. See Post iT, Request IP range
- Third, your vnet must be peer to Virtual Wan
How can I request for ZPA
Raise a demand using the ZPA request with ZPA details :
-
Tracibility Informations: those first field are important for us, allow us to correctly tag the environnement and apply some specific naming convention.
- Operantion: Add or Update
- Subscription ID: Privatised target resource Sub ID
- Business Units: Specify trigrame you are relate to
- Data classification: refer to Innovate or Industrialize environnement
- Project Name: relate to your Project
-
Technicals Informations: relate to the connection itself, resource, users, port.
- Users: List of authorized users (note: as mentioned in the IAM doc only internal identity are allowed: thalesdigital.io & thalesgroup.com ).
- Resource: IP and/or FQDN, relate to resouce you want to privatise
- Targets Port: Specify Proto and Port you want to use
Please Notify your project responsible name (for instance: tech lead of the subscription which host the target application) If you no longer need ZPA, you must notify us and ask for an offboarding Offboarding ZPA
Known limitation
VPN P2S + Service Account is not supported (anymore)
The Information System Security Policy imposes to use Multi-Factor Authentication anywhere. ZPA is used to avoid exposing a protocol that does not support MFA to internet.
A service account is, by design, a technical account. To do so, the MFA is disabled. Using ZPA with a service account does not follow the Trustnest security policy (ISSP): no MFA to access to internal ports; so we have decided to forbid this mechanism.
Depending on your use cases, we provide recommendations:
- Use case A: you share a laptop with multiple users (deployment or demo laptop)
- Use case B: you interconnect an on-premise infrastructure to a Trusnest environment
Recommendation for shared laptop - use case A
recommendation: Ask for a ZPA access to the pool of users accessing to the shared laptop.
ZPA is not linked to your laptop. You can mount the VPN based on your nominative identity.
Proof:
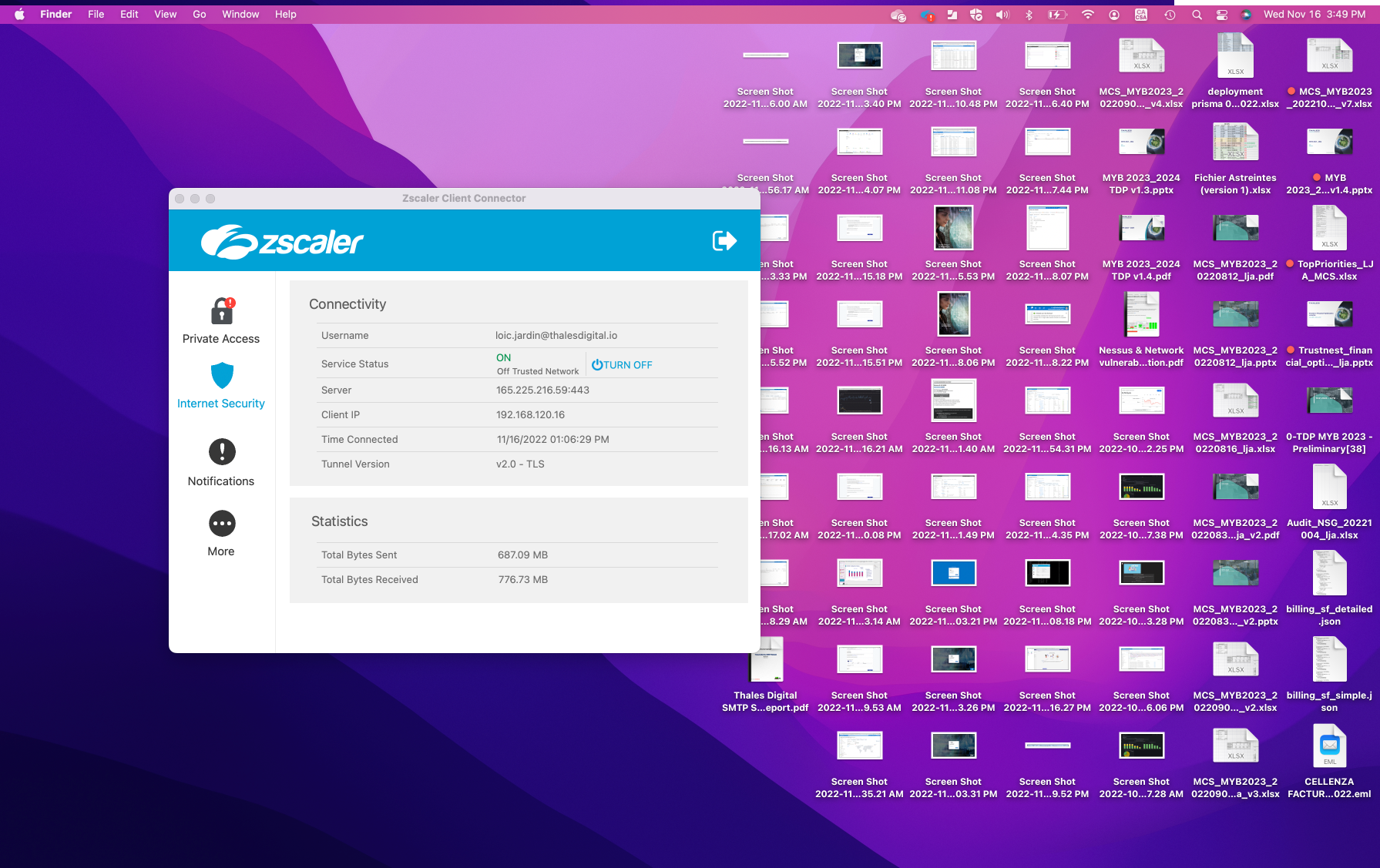
- ZPA used by user: loic
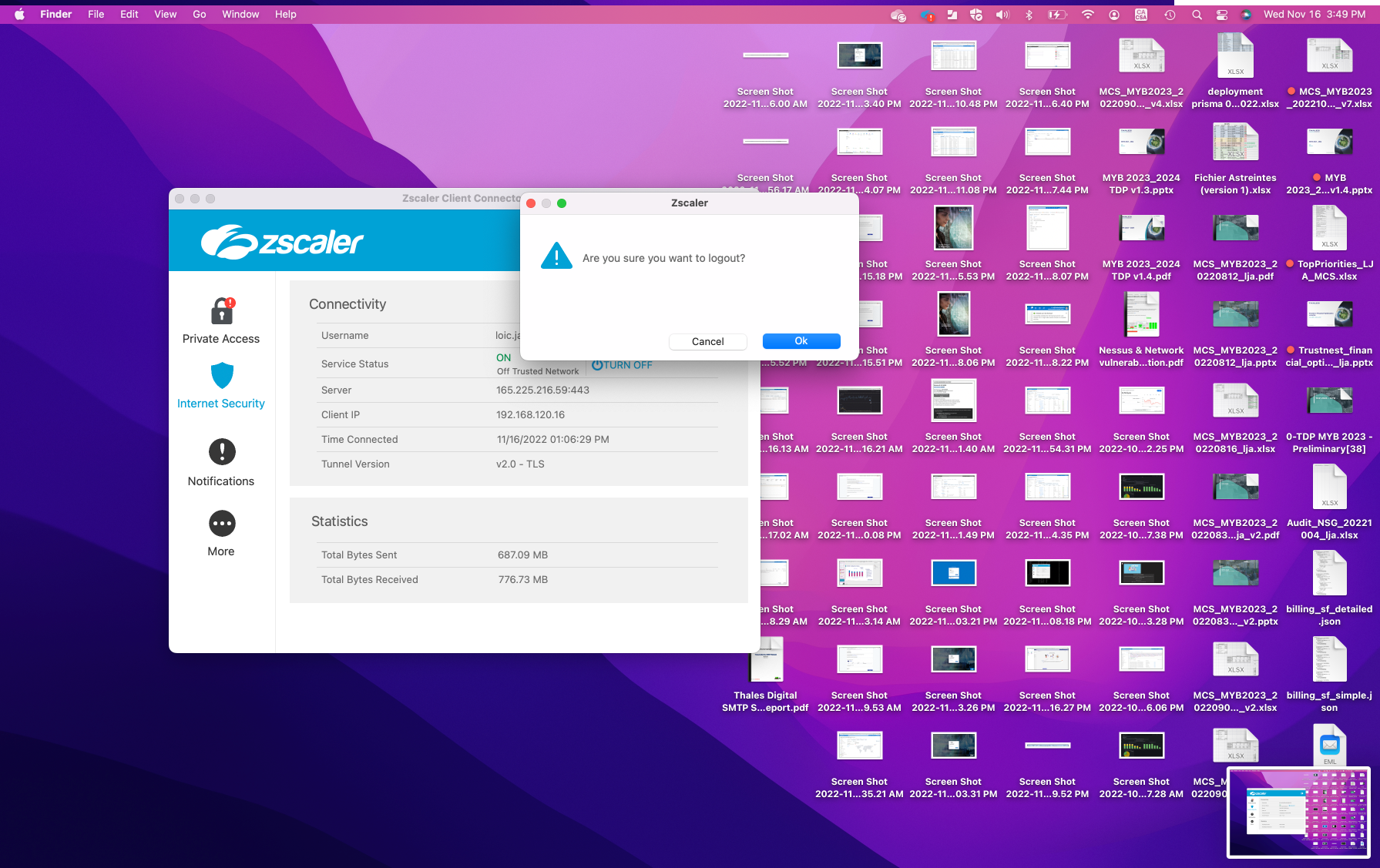
- logout

- login with a second user: sebastien on the same laptop
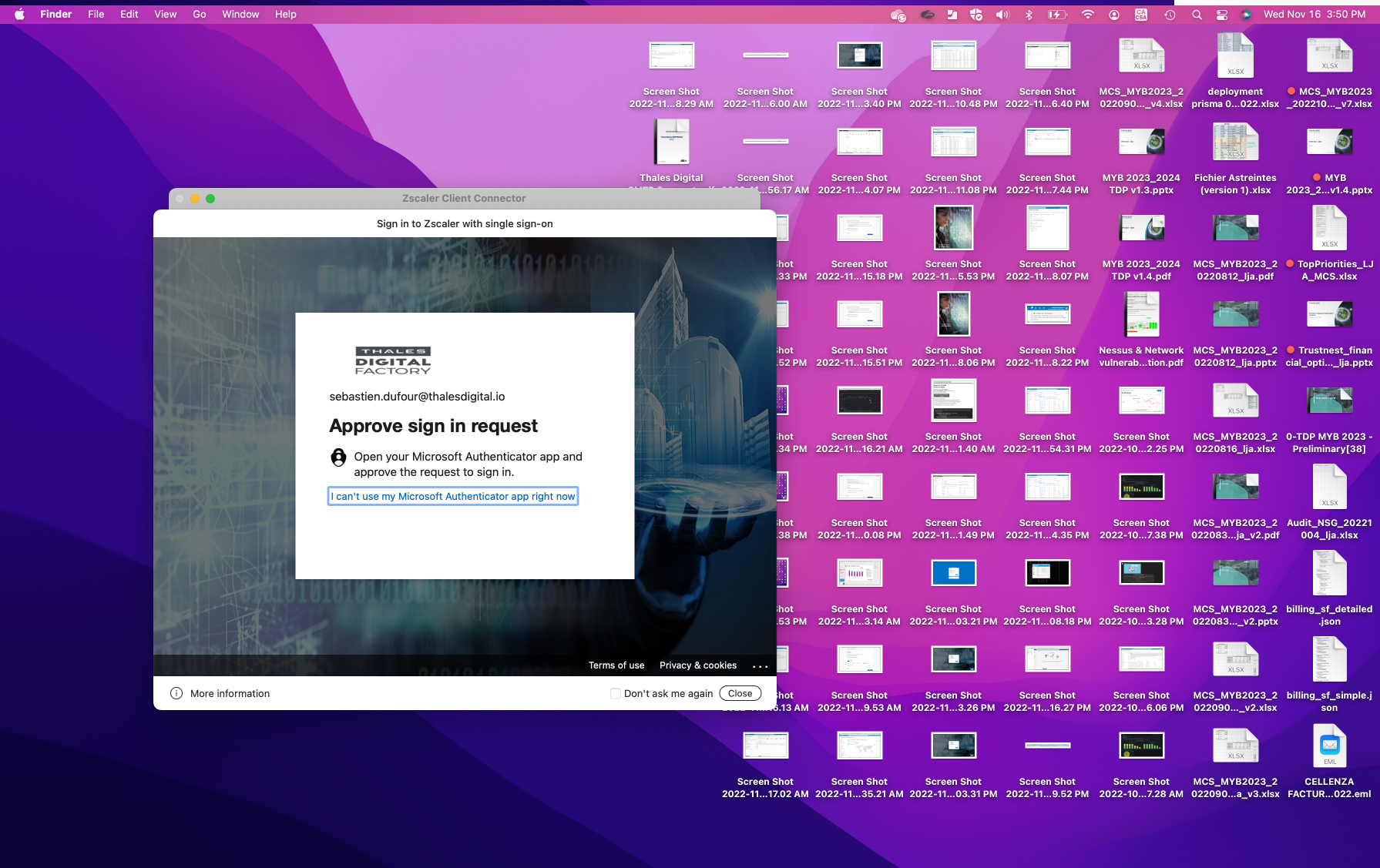
- whait ~2min, you should see the ZPA (private access module) appears, then login
Recommendation for on premise interconnection - use case B
recommendation: Contact your digital partner to identify your use cases and formalize a financial proposition.